Share
As edge computing and hardware capabilities enable incredible IoT innovation, device developers have a choice: develop a proactive approach to security or wait until a crisis forces you to invest a painful amount of time and resources into patching, forensic investigation, and, most critical—navigating an affected and unhappy customer base.
Consider the proliferation of IoT devices across nearly every part of daily life – IIoT, healthcare, fintech, automotive, etc. It’s not hyperbolic to say that if a cybersecurity attack against these devices is successful, the results can be catastrophic or life-endangering. Just think of the Mirai botnet creating a global botnet army, heart implants with known security vulnerabilities, or vehicles that can be commandeered remotely.
Historically, the software sector has focused on security much more heavily than hardware engineers, in part because hardware is perceived as generally more secure — states can be set, and components can be managed physically. But that assumption is changing, given the rise in both firmware complexity and connectivity. Security compliance requirements for connected devices are increasing throughout the world, like the United Kingdom’s recent mandate on minimum security. But overall regulations are pretty basic and quite inconsistent globally. Without clear industry-wide security standards that guide device security and legislation and regulation that require specific compliance requirements, individual developers and their companies are now effectively on the hook for securing devices.
It’s no longer just savvy to develop with security in mind—it’s critical— as the consequences of neglecting IoT device security are becoming increasingly evident. Aside from losing customer trust, companies now need to worry about legal and financial consequences or even getting their smart device banned in certain countries for good. For developers, this means prioritizing security from the initial design phase.
Prioritizing Security
Security should be integrated into the very fabric of your hardware design. Ignoring security until the last stages can lead to significant setbacks and potential compromises.
To ensure a robust security strategy from the start, here are a few basic steps that, if taken early, can prevent big headaches down the road.
- Start early: Begin building your security strategy during the initial development cycles. Address security concerns from the beginning to avoid costly and time-consuming redesigns later on.
- Secure, scalable over-the-air (OTA) updates: Cryptographically sign your firmware to ensure that only authorized updates can be loaded onto your devices. This prevents unauthorized access and strengthens the integrity of your device software. Additionally, you need to ensure that you have a consistent and repeatable way to deliver these updates.
- Employ cryptography: Secure the link between your device and the cloud using encryption protocols like TLS or MTLS. By implementing encryption standards, you safeguard the communication channels and protect data from interception or tampering.
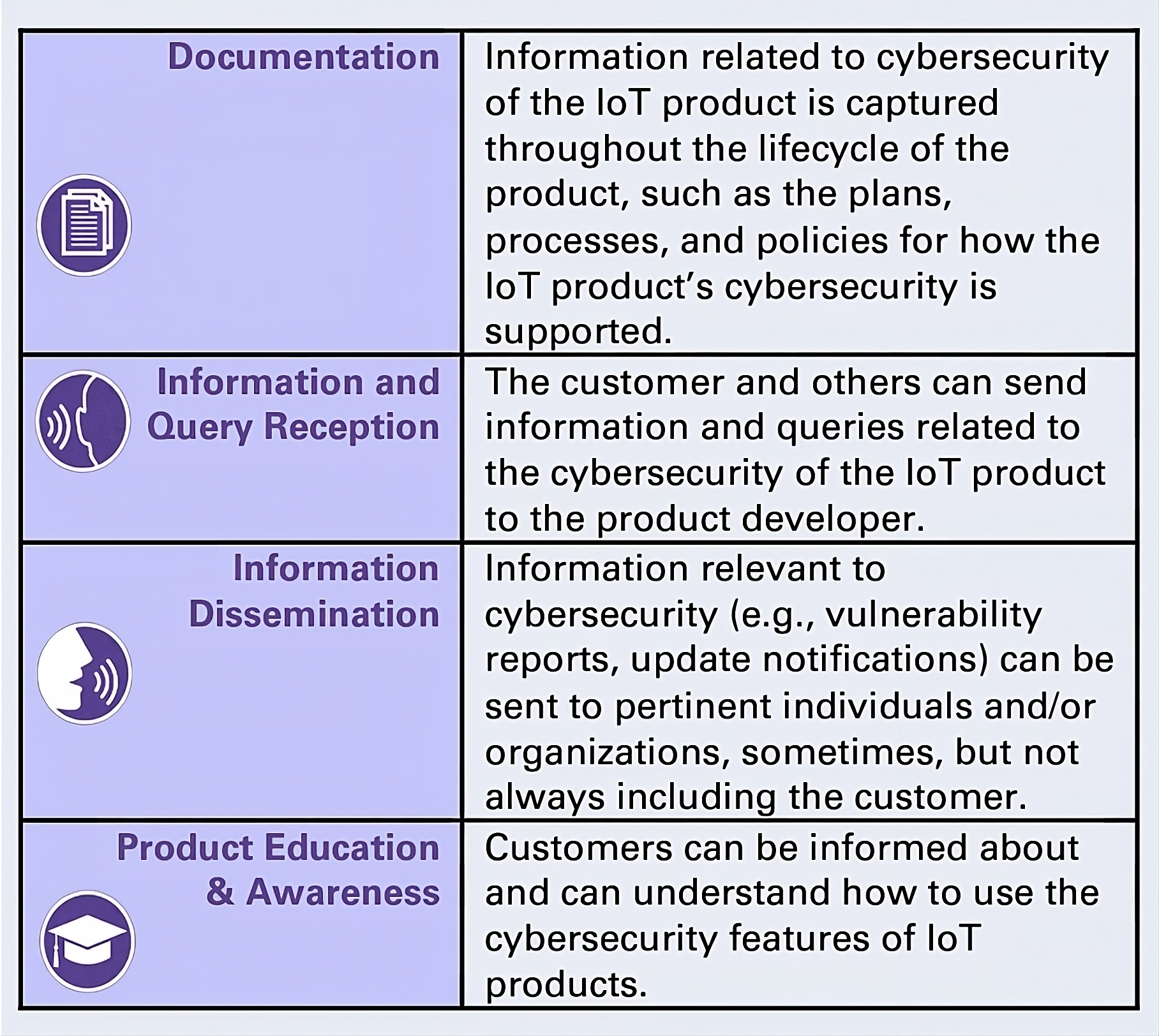
- Look to Country Regulations and Standards: As mentioned above, different countries are finally starting to put regulations in place. For example, in 2021, the United States Executive Order on Improving the Nation’s Cybersecurity NIST tasked NIST with developing practical recommendations for responsible IoT development. Last year, after broad industry input, NIST published its Profile of the IoT Core Baseline for Consumer Products, which offers specific cybersecurity criteria for IoT product developers. These guidelines provide basic direction for developers:
Building with security upfront and employing standards where possible will save you a ton of time rather than retrofitting less-than-ideal solutions at the end of the product cycle. For forward-thinkers, taking these recommendations to heart now isn’t just about being a responsible developer; it’s about getting ahead of where the industry will probably go. Increasing demand from both consumers and regulators means it is a matter of when, not if, stricter IoT industry regulation and compliance requirements will be developed and enforced. Taking these preemptive steps will save you from a terrible phone call years from now informing you that your device has been compromised.
Want to learn more about IoT device security? Watch this virtual panel discussion for more best practices for safeguarding your connected devices.
If you’re interested in learning more about Memfault, talk to our team.